1. Introduction
Lomads is a decentralized platform facilitating the creation and management of DAOs (Decentralized Autonomous Organizations). Its unique proposition lies in fostering community collaboration through features like multi-signature safes, SWEAT Points for contribution tracking, and an intuitive user interface. However, the inherent complexity of decentralized applications often introduces unique security risks. Consequently, Lomads commissioned a thorough pentest to ensure a secure foundation for its users and to bolster trust in its evolving ecosystem.
2. Engagement Scope and Objectives
- Attack Surface Analysis
We started by mapping all public endpoints tied to the DApp, identifying the functionalities exposed externally. This included the main web interface, the API endpoints, and critical features (DAO creation, settings, safe toggling, etc.). - Threat Modeling
We then performed threat modeling to determine potential adversarial paths—particularly focusing on access control vulnerabilities, injection attack surfaces, and the interplay between front-end and back-end validations. - Detailed Vulnerability Assessment
Using a black-box testing approach, we attempted to emulate real attackers with only the publicly available Lomads URL and documentation. The primary goal: uncover any misconfigurations, broken access controls, or logic flaws that could jeopardize DAO data or user funds. - Severity Classification & Actionable Reporting
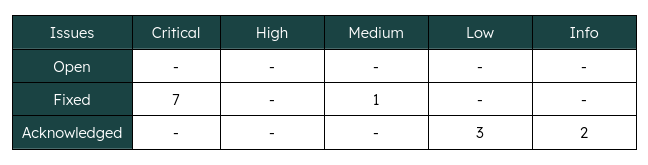
Each discovered vulnerability was assigned a severity rating (Critical, High, Medium, Low, Informational) based on the likelihood of exploitation and the potential impact on the platform. Accompanying remediation strategies were tailored to address root causes rather than superficial symptoms.
3. Methodology
-
- Reconnaissance and Mapping
- Automated Tools: Deployed Burp Suite to enumerate endpoints and scan for common weaknesses (XSS, SQLi, SSRF).
- Manual Recon: Investigated user flows, API documentation, and potential hidden or unprotected endpoints that might not be immediately visible to the public.
- Vulnerability Analysis
- Broken Access Control Tests: Checked if we could access, modify, or delete DAO resources without proper authorization.
- Input Validation Checks: Attempted various payloads (HTML/JS code in fields, large data strings) to identify XSS and DoS conditions.
- Business Logic Abuse: Explored the impact of spamming endpoints (e.g., DAO creation), toggling vital features (SWEAT Points, multisig safe states), and altering membership roles.
- Dependency Review: Investigated third-party libraries, discovering outdated versions with known CVEs.
- Proof-of-Concept (PoC) Exploits
Where relevant, we demonstrated real exploit paths (e.g., uploading malicious SVGs, unauthorized toggling of safes). This helped Lomads’ team grasp the gravity of each issue. - Reporting & Verification
- Initial Report: Delivered a comprehensive list of findings with recommended fixes.
- Follow-Up: Verified Lomads’ fixes and advised on best practices for future enhancements
- Reconnaissance and Mapping
4. Key Findings and Observations

4.1 Critical: Unauthorized DAO Detail Modification
-
- Observation: Attackers could alter various settings (e.g., DAO name, description, image) by intercepting and modifying requests to /api/v1/dao/{Dao_name}/update-details.
- Impact: Malicious actors could change critical metadata or sabotage governance processes by distributing false information.
- Root Cause: Broken access control checks at the server level. The application relied solely on front-end or session-based validations, which an attacker could bypass.
4.2 Critical: Unauthorized Multisig Safe State Toggle
-
- Observation: By switching the dao_name and safe_address fields, attackers could enable/disable the multisig feature or rename the victim’s safe without permissions.
- Impact: Disabling a multisig safe undermines the DAO’s primary security, exposing funds or contractual operations to single-signer vulnerabilities.
- Root Cause: Lack of server-side ownership checks and absence of multi-factor verification for critical operations.
4.3 Critical: XSS in Organization Creation (SVG Payload Injection)
-
- Observation: An uploaded SVG image could include embedded JavaScript, enabling persistent XSS whenever other users viewed that image.
- Impact: Unauthorized script execution could hijack sessions, steal user data, or perform actions on behalf of compromised accounts.
- Root Cause: Insufficient sanitization of file uploads and no robust Content Security Policy (CSP) to restrict inline scripts.
4.4 Critical: Unauthorized Disabling of SWEAT Points
-
- Observation: A malformed request allowed attackers to disable the SWEAT Points mechanism in any DAO, wiping out historical contributions.
- Impact: Loss of trust and significant disruption of DAO reward distributions.
- Root Cause: Lack of permission checks and enforced role management for toggling SWEAT Points.
4.5 Medium: Unlimited Input Size Vulnerability
-
- Observation: Certain fields (e.g., DAO profiles, descriptions) accepted arbitrarily large input, risking memory overload or potential DoS conditions.
- Impact: Attackers could degrade performance, cause prolonged loading, or even crash certain subsystems.
- Root Cause: Missing server-side validation or constraints on the maximum input length.
5. Recommendations and Remediations
-
- Robust Server-Side Access Controls
- Enforce role-based checks for every action.
- Validate that the request origin and the targeted resource (DAO, safe, etc.) match the authenticated user’s permissions.
- Input Validation and Sanitization
- Sanitize file uploads to strip malicious scripts from image headers.
- Use server-side validation to limit maximum input lengths and reject special character injections.
- Strict CSP and Secure Headers
- Implement Content-Security-Policy to disallow inline JavaScript and untrusted domains.
- Configure X-Frame-Options: DENY (or SAMEORIGIN if framing within the same domain is needed) and Strict-Transport-Security to enforce HTTPS.
- Proactive Rate Limiting
- Control repetitive requests on endpoints like DAO creation, updates, or any transaction-like API.
- Combine with CAPTCHA or verification steps for sensitive actions (e.g., toggling the multisig safe, disabling SWEAT Points).
- Version Management of Libraries
- Update jQuery (and other dependencies) to the latest stable releases.
- Set up automated alerts whenever dependencies have disclosed vulnerabilities.
- Operational Monitoring and Alerts
- Log all high-value operations (DAO creation, modifications, safe toggles).
- Implement real-time alerts for repeated failed login attempts, suspicious spikes in DAO creation, or abnormal request patterns.
- Robust Server-Side Access Controls
6. Positive Outcomes for Lomads
-
- Immediate Patching of Critical Issues
Lomads promptly resolved the most severe vulnerabilities (e.g., unauthorized toggling of multisig, disabling of SWEAT Points). These fixes restored user confidence and safeguarded the platform from exploit scenarios. - Enhanced Trust and Governance
By preventing malicious actors from tampering with DAOs, community stakeholders can rely on the authenticity of proposals, reward mechanisms, and governance decisions. - Future-Proof Security Culture
With improved developer training, a more stringent QA process, and the adoption of recommended security headers, Lomads has integrated secure development practices. This shift reduces the odds of reintroducing similar issues over time. - Strengthened User Base
Nothing boosts user adoption like the promise of security. Lomads’ prompt and transparent responses to identified flaws underscore a genuine commitment to user safety, fostering user loyalty and community growth.
- Immediate Patching of Critical Issues
7. Conclusion
The Lomads DApp penetration test showcased the unique challenges of securing a robust DAO management platform. By thoroughly examining access controls, input sanitization, rate-limiting, and outdated dependencies, we uncovered vulnerabilities that could have facilitated account takeovers, data corruption, or service disruptions.
Thanks to rapid remedial action, Lomads significantly elevated its security posture, reinforcing platform integrity and user trust. The lessons learned not only fix immediate issues but also catalyze sustainable security practices aligned with the fast-moving world of decentralized finance and blockchain-based governance.
This case study has been prepared by ImmuneBytes Security Specialists. For further inquiries or to discuss how our team can help fortify your DApp’s defenses, please get in touch.
