A Journey Through Code, Chaos, and Consensus
Picture a bustling marketplace with no single trusted authority at its centre. Everyone trades; everyone has a voice; everyone helps keep the records straight. This is what a blockchain aspires to be: a self-regulating engine of consensus, a living ledger that needs no sole middleman. Yet beneath this aspirational façade lies a complex piece of machinery that must trust, at the very least, its blueprint. And when we trust a blueprint, we must know exactly where its joints might creak and where its welds could fail.
This article focuses on assessing the backbone of blockchains—the internal mechanics that keep them humming. We’re not here to scrutinize a DeFi app’s interface or an NFT marketplace’s user experience. Instead, we’re zooming in on the infrastructure: the consensus layers, data integrity frameworks, network protocols, and modular components that give rise to entire ecosystems. At these deeper levels, a single overlooked assumption can topple the entire operation.
Consensus: Trust in a Distrusting Machine
At the heart of any blockchain is its consensus protocol. Without a reliable way for thousands of nodes to agree on a single source of truth, the entire system collapses. Proof-of-Stake (PoS) models, such as those in Cosmos-based chains, assume that most validators will behave; after all, they’ve staked their assets as collateral. But what if a cartel of validators quietly aligns their interests? What if the economic incentives become skewed, and collusion turns out to be more profitable than fairness?
Subtle Threats to Consensus:
- Validator Cartels: A small group of validators might form an alliance and, with enough combined voting power, rewrite transaction histories, finalize dubious blocks, or censor certain transactions. This covert cooperation undermines the chain’s integrity from within, even if it appears compliant on the surface.
- Attacks on Finality Windows: Many Byzantine Fault Tolerant (BFT) protocols have a “window” before finality is established. If an adversary can manipulate block propagation or network connectivity during this period, they might introduce forks or stall the consensus process, preventing the chain from reaching a stable historical record.
- Perverse Incentives and Misbehavior: A validator chasing higher profits might dodge punishment mechanisms or engage in subtle timing tricks. Over time, these cracks in the incentive structure widen, eroding trust and security.
Reinforcing the Foundations:
Projects often combine cryptographic proofs, strict slashing conditions, and random selection of validators (via VRFs) to keep adversaries guessing. Ethereum’s beacon chain and Cosmos’s Tendermint algorithm, for instance, implement multiple layers of voting rounds and finality checkpoints. Like a fortress with many walls, each layer limits the damage an attacker can inflict.
The Data Layer: Memory, Availability, and the Ghosts of Transactions Past
A blockchain is more than a chain of blocks. It’s a dynamic memory system—one that must faithfully record every transaction’s effect on accounts, smart contracts, and governance parameters. When data is missing, corrupted, or withheld, the chain’s promises unravel. For instance, modules built on the Cosmos SDK rely on accurate, timely data not just locally but also across entire Inter-Blockchain Communication (IBC) networks. Even a slight hiccup in data availability can cause appchains to lose sync or fail to update their state machines correctly.
Key Threats to Data Availability:
- Selective Withholding of Transactions: If certain nodes censor transactions by not broadcasting them, mempools become distorted. This may give some market participants unfair advantages or render the network partially unusable.
- Historical Data Loss and Pruning Mistakes: Over time, blockchains prune old data to remain efficient. However, an error in pruning logic might delete essential historical records or invalidate previous state transitions. Losing this history is like losing one’s legal documents—without them, current claims are far less credible.
- Data Availability Failures in Modular Architectures: Advanced scaling solutions, rollups, and appchains depend on complete historical data. If a node withholds state updates, dependent chains can grind to a halt, leaving users stranded and eroding trust.
Mitigation Strategies:
- Data Availability Proofs and Erasure Coding: These techniques ensure that all nodes collectively hold a complete and verifiable dataset, making it harder to selectively withhold information.
- Encrypted Mempools: Encrypting transaction data before inclusion on-chain prevents nodes from censoring or manipulating transactions based on their content.
Rigorous IBC Verification: Careful verification of IBC messages and fallback strategies for cross-chain acknowledgements ensure that when one chain whispers state changes to another, the message arrives intact and truthful.
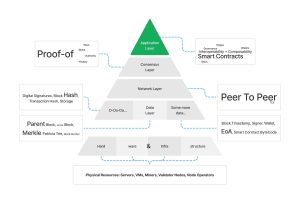
The Network Layer: Where Decentralization Meets the Real World
Blockchains rely on peer-to-peer networking to spread information quickly and reliably. But the real world is messy—there are latency differences, malicious nodes, and attackers who aim to isolate honest participants. Even in a decentralized setting, controlling the flow of information can yield formidable advantages.
Even in fully decentralized protocols, network-level threats can isolate nodes, delay blocks, or disrupt synchronization:
- DDoS Barrages and Latency Exploits: High-frequency trading appchains, for example, depend on low-latency updates. A well-timed DDoS can slow block propagation, letting a cunning attacker reshape transaction order. Over time, these delays and disruptions can lead to subtle market manipulations.
- Eclipse Attacks: Imagine a scenario where a validator (or a small set of them) only sees a carefully curated subset of the network. The attacker feeds them outdated blocks or censors certain transactions entirely. Trapped in their private bubble, the victim operates in a different reality than the rest of the network.
Building a Resilient Communication Web:
The network layer connects the distributed nodes of a blockchain through peer-to-peer (P2P) communication. Nodes gossip transactions, share blocks, and validate states. But decentralized doesn’t mean untouchable—the network layer is an attack surface, and its weaknesses ripple upward to consensus and data layers.
Countermeasures often come down to robust peer selection, maintaining a diverse set of connections, and constant latency and availability monitoring. Some chains also lean on partially centralized “bootstrapping” services or identity-staking systems to limit the impact of Sybil attacks—though this must be balanced carefully with the ideals of decentralization.
- Network Diversification: Ensure nodes maintain multiple, geographically distributed peer connections to avoid isolation.
- Anti-Sybil Mechanisms: Use identity validation (e.g., Proof of Stake weights) to limit malicious nodes’ influence.
- Latency Testing: Continuously monitor node latency and propagation times to detect anomalies in network communication.
Modularity in Blockchains:
Cosmos SDK has revolutionized blockchain architecture by enabling custom appchains with modular components. Modules for user management, governance, staking, and liquidations allow developers to “build their chain.” Yet this modularity also introduces fragmented vulnerabilities.
Key Threats in Modular Chains:
The flexibility of appchains comes with unique risks:
- Collateral Module Underflows: Custom liquidation logic may miscalculate health scores, delaying liquidations and causing cascading insolvencies.
- IBC Message Loops: Improper handling of cross-chain acknowledgments can deadlock communication channels, as observed in earlier Cosmos vulnerabilities.
- State Sync Failures: Modules tracking user funds or orders may experience gas exhaustion or desynchronization, freezing critical operations.
Mitigation Strategies:
- Invariant Testing: Implement rigorous fuzz testing and property-based tests for all custom modules (collateral, vesting, health scoring).
- Loop Safety Validation: Ensure cross-chain IBC message handlers avoid unbounded loops.
- Redundant Monitoring: For modules tracking state (e.g., order books), introduce state consistency checks across nodes.
Developers must rigorously test each module, ideally using fuzz testing, property-based testing, and formal verification tools where possible. Clear specifications, thorough audits, and fallback safety mechanisms (like timeouts on IBC acknowledgements) can prevent these localized malfunctions from spreading like viruses through the system.
Conclusion: Threat Modelling Is Non-Negotiable
A blockchain doesn’t break at the surface—it fractures from the inside. When threat modeling, the focus must be on the protocol bones: consensus algorithms, network stability, data availability, and appchain modules. Every layer must be systematically dissected, its assumptions challenged, and its adversarial behavior modeled.

